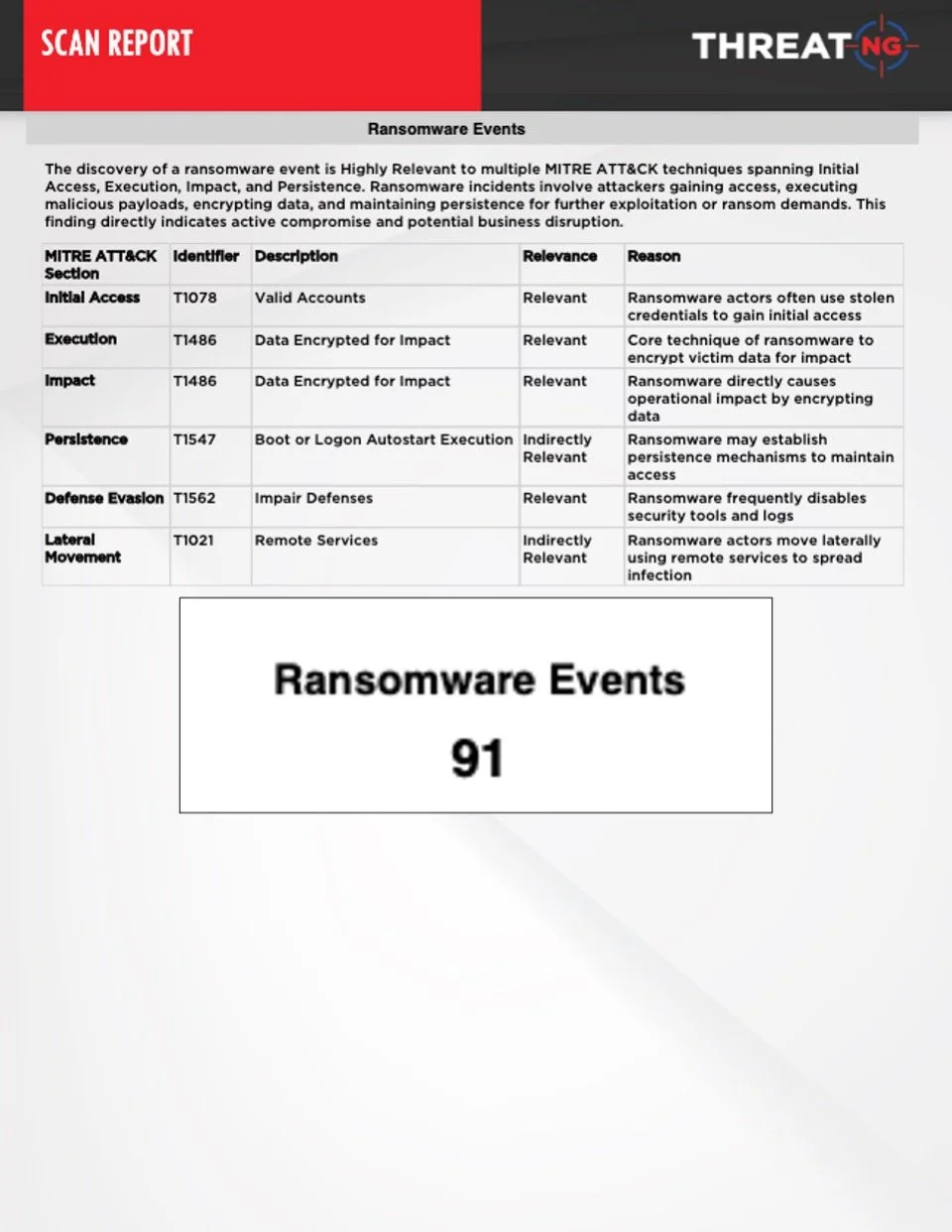
MITRE ATT&CK® Mapping
From Boardroom Fear to Boardroom Confidence: Master Your Attack Surface with MITRE ATT&CK® Mapping
As a CISO, you operate in two worlds: the technical world of vulnerabilities and exploits, and the strategic world of the boardroom. The problem is, they don’t speak the same language. Your team is overwhelmed by thousands of alerts and high CVSS scores, while your board poses questions that your data can't answer: "Are we protected from the ransomware attack that just hit our competitor?" Presenting spreadsheets of vulnerabilities is met with polite indifference because it fails to tell a story of business risk. ThreatNG’s MITRE ATT&CK Mapping capability is the translator you've been missing. It automatically converts the raw noise of your external attack surface into a straightforward, strategic narrative of adversary behavior, empowering you to stop managing lists and start leading a proper, threat-informed defense.
From Tactical Noise to Strategic Narrative: Prioritize Real Threats, Command the Boardroom, and Outmaneuver the Adversary

End the Tyranny of the CVSS Score and Prioritize with Precision
Your security team is wasting thousands of hours and millions of dollars chasing vulnerabilities that will never be exploited. The reality is that less than 4% of all published CVEs are used in real-world attacks, yet traditional tools force your team to treat every high CVSS score as a five-alarm fire. This creates alert fatigue, team burnout, and a false sense of security while the simple misconfigurations that attackers actually use are ignored. Our MITRE ATT&CK Mapping shatters this broken model. By automatically correlating each external finding—from a leaked credential to an open port—to a specific adversary TTP, we give you the context to prioritize what truly matters. Stop asking "How severe is it?" and start asking "Will an attacker use this against me?". This marks a shift from chasing ghosts to focusing resources on disrupting the most likely attack paths.
Speak the Language of the Boardroom and Justify Your Security Investment
Walk into your next board meeting with unshakable confidence. The communication gap between CISOs and the board is the single greatest threat to your program and your career. Board members suffer from "complexity aversion bias"; they don't want technical jargon, they want to understand business impact and risk in financial terms. MITRE ATT&CK is the globally recognized "common lexicon" that bridges this divide. Our capability provides you with a board-ready, visual matrix of your organization's specific exposures. You can now transform the conversation from "We patched 500 CVEs" to "We have closed the three primary 'Initial Access' pathways used by ransomware groups targeting our industry, measurably reducing our financial risk exposure." This is how you secure budget, earn credibility, and elevate your role from a technical manager to a strategic business leader.

Think Like an Attacker, Defend Like a Strategist
A reactive security posture is a losing strategy. To win, you must anticipate the adversary's next move. Our External Adversary View with MITRE ATT&CK Mapping gives you the power to see your organization not as you do, but as an attacker does. We don't just show you a list of weaknesses; we reveal the potential attack chains an adversary could build by linking them together. By understanding how a forgotten subdomain could be used for T1190 (Exploit Public-Facing Application) or how missing email security directly enables T1566 (Phishing), you can move beyond patching and begin proactively disrupting adversary playbooks. This is the essence of a threat-informed defense: using your enemy's tactics against them to build a more resilient, proactive, and effective security program.
The "So What?" Solved: Crystal-Clear Reports Detailing Every MITRE ATT&CK Mapping
ThreatNG moves beyond simply listing your external findings; we provide the crucial context that makes the data actionable. Our easy-to-read reports provide a transparent, detailed breakdown of how each specific weakness on your attack surface aligns with the MITRE ATT&CK framework. For every finding, such as a "Subdomain Missing a Content Security Policy," we provide the specific technique (e.g., T1190: Exploit Public-Facing Application) and the explicit rationale, noting that the missing header enables client-side injection attacks that adversaries use for initial access. This granular detail transforms abstract data into an easy-to-understand narrative of your true risk.
ThreatNG MITRE ATT&CK® Mapping: Frequently Asked Questions
This FAQ is designed for Chief Information Security Officers (CISOs), Heads of Security Operations, and other security leaders to understand the strategic and operational value of ThreatNG's MITRE ATT&CK Mapping capability.
The Basics: Understanding the Capability
-
ThreatNG's MITRE ATT&CK Mapping is an intelligence feature within the External Adversary View. It automatically translates the raw, technical findings from your external attack surface—such as misconfigurations, vulnerabilities, and leaked credentials—into the globally recognized MITRE ATT&CK framework. This provides immediate context, showing you how an adversary would use these weaknesses against you by mapping them to specific tactics, techniques, and procedures (TTPs).
-
The MITRE ATT&CK framework is a globally accessible, curated knowledge base of adversary tactics and techniques based on real-world observations. Think of it as an encyclopedia of attacker behavior. It's important because it creates a common language for security professionals, threat intelligence teams, and executives to discuss and understand cyber threats. Instead of discussing abstract vulnerabilities, you can focus on specific adversary behaviors that require defense, such as "Initial Access" via "Phishing" (T1566) or "Persistence" via "Valid Accounts" (T1078).
The Problem: Why This is a “Need-to-Have”
-
Your external attack surface is the adversary's entry point. While many tools use ATT&CK for internal threat detection (post-compromise), ThreatNG applies it to your external posture, allowing you to see your organization as an attacker does before they get in. This proactive, "outside-in" view enables you to disrupt the attack chain at the earliest possible stage—Reconnaissance and Initial Access—making it far more effective and less costly than addressing an active breach.
-
No, it does the opposite. This capability is designed to reduce noise by adding context. The core problem for most security teams isn't a lack of data, but "prioritization paralysis" caused by too many alerts without a clear risk context. Instead of providing another list of findings, our mapping identifies which ones constitute a viable attack path. This allows your team to stop chasing thousands of low-risk issues and focus its limited resources on the handful of weaknesses that adversaries are most likely to exploit.
-
No, it's no longer sufficient. The Common Vulnerability Scoring System (CVSS) measures the theoretical severity of a vulnerability in a vacuum, not the real-world risk to your organization. A CVSS score doesn't know if a vulnerability is on a critical, internet-facing asset, nor does it tell you if it's actively being exploited. Research shows that only a small fraction of all disclosed vulnerabilities are ever actually exploited. Relying solely on CVSS means your team is likely wasting thousands of hours and significant budget on non-essential vulnerabilities, while critical risks remain buried in the backlog.
The Solution: How We Make Your Life Better
-
This is one of the most powerful use cases. Board members and C-suite executives often struggle with technical jargon and metrics like CVSS scores, leading to a "complexity aversion bias". The MITRE ATT&CK framework provides a shared, strategic language to bridge this communication gap.
Instead of saying, "We have 50 critical vulnerabilities," you can now say, "Our external posture shows a high exposure to 'Initial Access' techniques favored by ransomware groups. We've identified and are remediating the three specific weaknesses—leaked credentials and an open RDP port—that enable these exact adversary playbooks." This shift transforms you from a technical manager into a strategic risk advisor, boosting credibility and justifying security investments with clear, business-focused language.
-
It provides a defensible, data-driven methodology for prioritization. By seeing which findings map to attacker TTPs, your team can immediately focus on what's most important. For example:
Leaked credentials on the dark web are no longer just a data point; they are a direct pathway for an attacker to achieve T1078 (Valid Accounts) for Initial Access.
A missing DMARC record is not just a minor email setting; it's a critical gap that enables T1566 (Phishing), a primary vector for ransomware.
An open RDP port isn't just a configuration issue; it's an open door for T1021 (Remote Services), used for both Initial Access and Lateral Movement.
This threat-informed approach ends the "wild goose chase" for high CVSS scores, reduces team burnout, and allows your analysts to make a measurable impact on risk reduction.
-
Our platform uses a proprietary intelligence engine that correlates the thousands of data points gathered during our external, unauthenticated discovery process with the ATT&CK knowledge base. This isn't a simple keyword match. The mapping is based on a deep understanding of adversary methodologies and real-world threat intelligence. For every finding, we provide the reasoning behind the mapping, turning every piece of data into actionable adversary intelligence.
-
Absolutely. This is one of the most powerful applications of the capability. Instead of relying on generic threat intelligence, ThreatNG allows you to map your organization's specific, real-world exposures directly to the playbooks of known adversaries.
Here’s how it works with real-world examples:
Defending Against FIN7: The threat group FIN7 is well-known for using spear-phishing campaigns for initial access, which corresponds to MITRE ATT&CK technique T1566 (Phishing). If ThreatNG detects that your organization lacks DMARC or SPF email security records, our capability automatically maps this finding to T1566. This instantly shows you that a simple email security misconfiguration is leaving a door wide open for one of FIN7's primary attack vectors.
Defending Against APT29 (Cozy Bear): The group APT29 often gains its initial foothold by using compromised credentials to simply log in as legitimate users—a technique known as T1078 (Valid Accounts). When ThreatNG's Dark Web monitoring detects your company's credentials for sale, it not only alerts you to the leak but also maps that finding directly to T1078. You can immediately see your specific exposure to APT29's methods and prioritize action.
The External Adversary View enables you to filter your entire attack surface based on the known TTPs of these and other groups, such as the Lazarus Group. This transforms the abstract question, "Are we vulnerable to the group in the headlines?" into a concrete, data-driven answer. You can proactively identify and remediate the exact external weaknesses that your most likely adversaries are actively looking to exploit.
Getting Started
-
The MITRE ATT&CK Mapping capability is a core, integrated part of the ThreatNG External Adversary View. There is no complex setup required. Because our platform is purely external and unauthenticated, the mapping is automatically generated as soon as our discovery and assessment of your attack surface is complete. The results are presented in an intuitive, visual matrix that is immediately ready for analysis and reporting.