Domain Name Permutations
Protecting Your Digital Identity: The Power of Proactive Domain Permutation Analysis
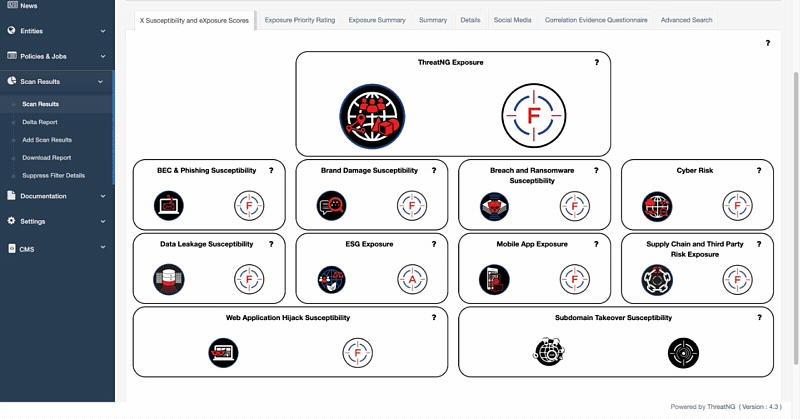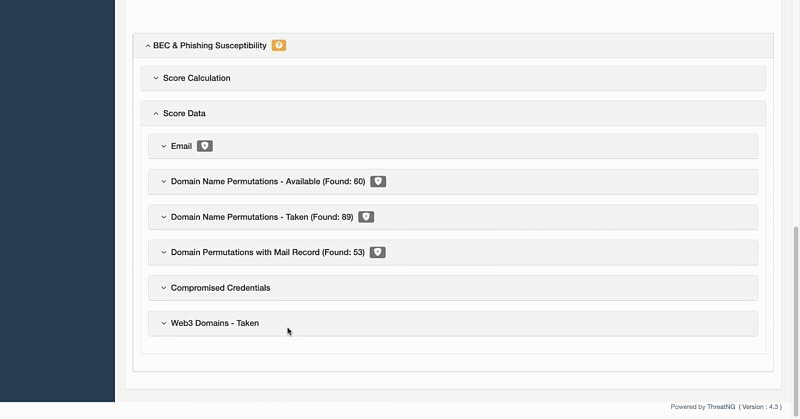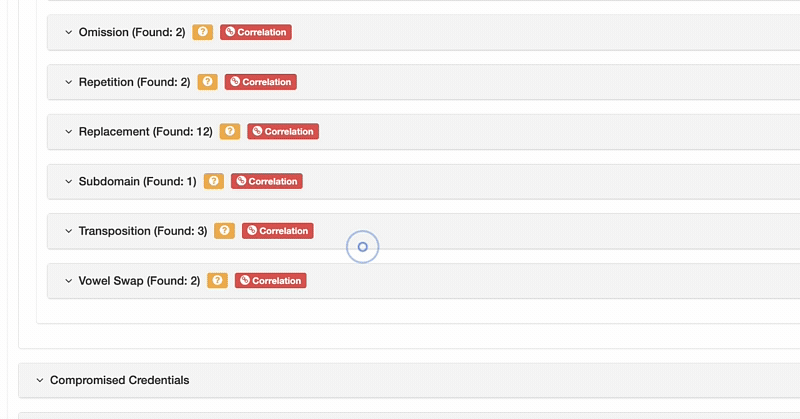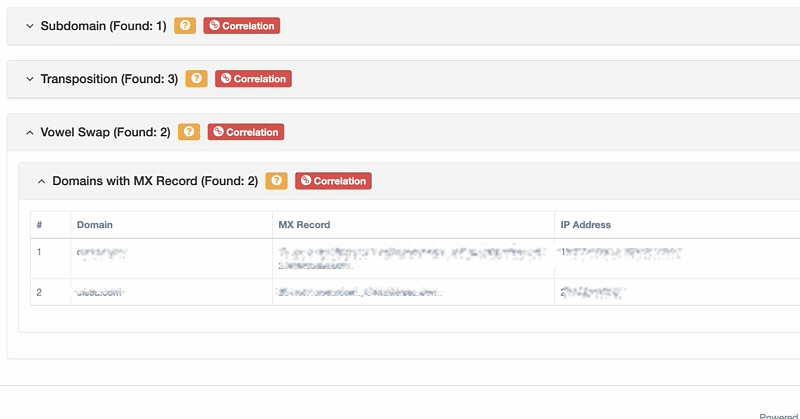
ThreatNG's Domain Name Permutations capability provides a comprehensive defense against digital risks by proactively detecting and analyzing potential domain variations. As part of its DNS Intelligence module, this capability uncovers hidden threats, identifies look-alike domains, and helps protect your brand from a full spectrum of attacks, including phishing, brand abuse, and counterfeiting. ThreatNG predicts how attackers might attempt to exploit your brand by automatically generating and uncovering a full range of domain manipulations, from homoglyphs and bitsquatting to TLD-swaps and subdomain impersonation. The platform enhances its threat detection by allowing you to add a custom list of user-defined Top-Level Domains (TLDs) and keywords, ensuring the analysis is always relevant to your unique digital footprint. For every domain it flags as taken, ThreatNG provides the associated IP address and mail record, giving you the critical information needed to respond to any threat.
Uncover All Domain Manipulations with ThreatNG
ThreatNG's Domain Name Permutations can identify and group available and taken domain permutations and manipulations. For those that are taken, it provides the associated IP address and mail record. ThreatNG can uncover all of the following domain permutations for available and taken domains, and it categorizes them to give greater context and actionable intelligence.

Categorizing domain permutations is essential because it helps you understand the specific methods attackers use to create fraudulent domains, allowing for more targeted and efficient threat detection and response. It also enables you to prioritize risks, as particular categories, like homoglyphs or bitsquatting, may pose a higher risk due to their use in sophisticated phishing attacks. By categorizing, the platform helps you quickly differentiate between a simple misspelling and a deliberate, malicious attempt at brand impersonation, enabling you to allocate resources more effectively to address the most critical threats.

Additions / Domain Stuffing
Adding characters to the end of a domain name to create a fraudulent site. Examples:
mycompany-login.commycompany-service.com
Dictionary Additions / Domain Suffixing
Appending a familiar or common word to the domain to impersonate a service. Examples:
mycompany-support.commycompany-help.com
Hyphenations
Inserting a hyphen into the domain name to make it appear legitimate. Examples:
my-company.commy-company-inc.com
Replacements
Replacing a character with a similar-looking one from the same character set, often a number for a letter. Example:
m9company.com(replacing the letterywith the number9)myc0mpany.com(replacing the letterowith the number0)
Substitutions
Swapping a character with a visually similar one, such as replacing a letter with a number.
mycompony.com(the letter 'a' is replaced by a visually similar but different key, 'o').mycompaqy.com(the letter 'n' is replaced by 'q' because of their proximity on a QWERTY keyboard, making it a common typo).
Transpositions
Swapping the order of two adjacent characters in the domain name. Examples:
mcyompany.comymcompany.com
Bitsquatting / Digital Typo
Creating a domain that is off by a single bit, resulting in a similar-looking, misspelled name. Examples:
gycompany.comgogle.com
Homoglyphs / Visual Deception
Using characters that look visually identical or similar to the legitimate ones, often from a different character set. Examples:
mγcοmpany.com(using a Cyrillic 'ο')exampIe.com
Subdomain Impersonation
Creating a subdomain that impersonates a legitimate service or brand. Examples:
security.mycompany.comlogin.mycompany.com
TLD-Swap / TLD Impersonations
Using a different Top-Level Domain to mimic the original. Examples:
mycompany.netmycompany.co
Vowel Swaps / Vowel Substitutions
Swapping a vowel with another. Example:
mycompuny.commycompanee.com

Beyond the Basics: Advanced Digital Risk Protection with Customizable Permutations
Domain Name Permutation investigations are further enriched by allowing users to define and use additional Top-Level Domains (TLDs) and Targeted Key Words.

Proactive TLD Discovery: Your Defense Against Digital Threats
ThreatNG's Domain Name Permutations capability enhances the detection of digital footprint expansion and brand impersonations by using both a pre-packaged set and a customizable list of user-defined Top-Level Domains (TLDs). For instance, you could add new TLDs like .app or .store to a search, or even country-specific ones like .de or .jp to ensure your investigation is more targeted. This comprehensive approach allows for more focused investigations into potential security gaps and reputational risks across your digital ecosystem.
You can use the pre-built lists or add your own to align with new business initiatives or to assess new partners. This flexibility ensures that the investigation of domain permutations remains relevant to your organization’s unique digital exposure and risk posture.
The platform includes a pre-built selection of TLDs, organized into the following categories:
Generic TLDs: The most common and unrestricted top-level domains, originally meant for general use. Examples include .com, .net, and .org.
Classic gTLDs (Generic Top-Level Domains): The original and most widely recognized generic top-level domains. Examples include .com, .net, and .biz.
Sponsored and Restricted gTLDs (Generic Top-Level Domains): These domains are reserved for specific organizations or communities, requiring the registrant to meet particular criteria. Examples include .gov for U.S. government entities and .mil for the U.S. military.
New gTLDs (Generic Top-Level Domains): This category includes recently created TLDs that are more specific to industries, locations, or creative purposes. Examples include .tech for industry-specific sites and .london for geographic ones.
gccTLDs (Generic Country Code Top-Level Domains): These country code TLDs are not restricted to their specific countries and are often used as generic alternatives to a .com domain. Examples include .io, .co, and .tv.
Internationalized Domain Names (IDNs): IDNs use characters from non-Latin alphabets, enabling domain names to be created in languages such as Arabic, Cyrillic, or Chinese. An example is .рф, which is used for Russia.
Country Code TLDs (ccTLDs): These are two-letter top-level domains assigned to specific countries, territories, or sovereign states. Examples include .us for the United States, .uk for the United Kingdom, and .de for Germany.
Major Global Economies: These are the country code TLDs for the largest and most influential economies in the world. Examples include .us (United States), .uk (United Kingdom), and .de (Germany).
European Countries: Country code TLDs for nations located across the continent of Europe include .it (Italy), .fr (France), and .es (Spain).
Asian Countries: For countries within the continent of Asia, the TLDs are .jp (Japan), .kr (South Korea), and .cn (China).
South American Countries: The country code TLDs for nations located in South America are .br (Brazil), .ar (Argentina), and .cl (Chile).
African Countries: The country code TLDs for countries on the continent of Africa are .za (South Africa), .ng (Nigeria), and .eg (Egypt).
Other/Miscellaneous ccTLDs: These are country code TLDs that have gained popularity for purposes beyond their original geographic assignment. Examples include .io (popular with tech startups) and .co (often used as an alternative to .com).
Protecting Your Digital Footprint: Dynamic Keyword Permutations for Risk Detection
ThreatNG's Domain Name Permutations capability helps identify look-alike domains and impersonations of your online presence. It does this by incorporating a curated set of targeted keywords while also allowing you to add your own keywords to search for domain manipulations. For example, you can include keywords like "login" to detect fraudulent login pages or "pay" to find fake payment portals. This comprehensive approach enables more focused investigations into potential digital threats and reputational risks.
You can choose from pre-built keyword lists or add your own to align with new business initiatives or assess potential partners. This flexibility ensures that the investigation of domain permutations remains relevant to your organization’s specific digital exposure and risk tolerance.
The platform includes a pre-built selection of keywords, organized into categories:
Website & Infrastructure: Words like www, http, and cdn describe the technical foundation and structure of a website or online service. Examples:
mycompany-cdn.com & www-mycompany.comBusiness & Financial: These terms are related to commercial or financial transactions and operations within a system. Examples include business, pay, and payment. Examples:
mycompany-pay.com & mycompany-business.comAccess Management: Terms like 'access' and 'auth' relate to the control of who can access a system and what resources they can use. Examples:
mycompany-auth.com & mycompany-access.comAccount Management: This group encompasses terms such as account and signup, which relate to the administration and maintenance of user accounts. Examples:
mycompany-signup.com & mycompany-account.comSecurity Verification: Used to confirm a user's identity, these terms include 'confirm' and 'verify'. Examples:
mycompany-verify.com & mycompany-confirm.com
User Portals: Terms associated with the interface where users manage their information and access services are login and portal. Examples:
mycompany-login.com & mycompany-portal.com
Offensive Language: Terms in this category are typically used to insult or are considered vulgar and profane.
Critical Language: This group comprises terms that convey disapproval or negative judgment, but are generally less profane than offensive language. Examples:
mycompany-awful.com & mycompany-bad.comAction Calls: This category encompasses terms typically used to incite or describe a protest or strong opposition. An example is boycott. Example: boycott-mycompany.com

ThreatNG's ability to generate Domain Name Permutations and check their availability and associated IP addresses is a powerful capability for both External Attack Surface Management and Digital Risk Protection. Here's how:
Proactive Threat Identification: Domain name permutations can identify look-alike domains and potential threats before they become active attacks, helping you shrink your attack surface.
Comprehensive Coverage: This capability uncovers a full range of domain manipulations, including bitsquatting, homoglyphs, and TLD-swaps, to provide a complete view of your external attack surface.
Actionable Intelligence: For every fraudulent domain, ThreatNG provides the associated IP address and mail record, giving you the specific details you need to investigate and respond.
Proactive Threat Detection: DRP benefits from domain permutation analysis by proactively identifying potential digital threats before they escalate into attacks, allowing for a preemptive defense against various online risks.
Comprehensive Digital Footprint Coverage: This capability provides DRP with a complete view of an organization's digital footprint by uncovering and monitoring a wide range of domain manipulations, including those that are not immediately obvious.
Actionable Intelligence: DRP gains the ability to respond swiftly to threats, as the analysis provides specific data, such as IP addresses and mail records for taken domains, which is critical for incident response and mitigation.

Beyond Security: Domain Name Permutations for Brand Protection, Due Diligence, and Third-Party Risk Management
ThreatNG's Domain Name Permutation analysis isn't just for security teams. It's a powerful solution for safeguarding your brand reputation, conducting thorough due diligence, and managing third-party risk. Uncover hidden threats to your brand, gain a comprehensive view of your vendors' digital footprint, and confidently make informed decisions. Discover how ThreatNG's domain permutation capabilities can benefit your organization across these critical areas.
Brand Protection
Brand Impersonation Defense: Domain permutation analysis directly benefits brand protection by actively finding and flagging look-alike domains and brand impersonations, which helps safeguard your reputation and maintain customer trust.
Counterfeit and Fraud Prevention: By identifying domains that mimic your brand, you can prevent the creation of fraudulent websites used for selling counterfeit goods or running scams that would otherwise harm your brand's integrity and revenue.
Global Monitoring and Customization: This capability allows brand protection teams to customize their monitoring to include specific TLDs and keywords relevant to their marketing campaigns, new products, or global presence, ensuring a tailored and effective defense.
Due Diligence
Pre-Acquisition and Partnership Vetting: The capability helps you quickly vet potential partners, vendors, or acquisitions by revealing suspicious domains that could indicate a history of malicious activity or security issues.
Comprehensive Digital Footprint Assessment: It allows you to gain a thorough understanding of an organization's full digital presence and potential vulnerabilities before you enter into a business relationship with them.
Informed Decision-Making: By providing precise data on potential risks, you can make more informed decisions about whether to move forward with a partnership or acquisition and negotiate terms based on a clear risk assessment.
Third-Party Risk Management
Ongoing Monitoring of Partners: Domain name permutation analysis enables continuous monitoring of your third-party ecosystem, allowing you to quickly detect any new look-alike domains or fraudulent sites that a malicious actor could create.
Supply Chain Threat Identification: It helps you uncover potential threats that could compromise your supply chain through a third party's digital footprint, ensuring your ecosystem remains secure.
Risk Posture Validation: The capability provides objective, external data to validate a third party's security posture and ensure their claims about brand protection and security are accurate.
Domain Name Permutations Frequently Asked Questions (FAQs)
-
The ThreatNG Domain Name Permutations capability proactively detects and analyzes potential domain variations to uncover hidden threats and identify look-alike domains. It automatically generates and analyzes a wide range of domain manipulations, such as homoglyphs, bitsquatting, insertions, omissions, and TLD-swaps. The tool can identify and group both available and taken domain permutations, and for those that are taken, it provides the associated IP address and mail record.
-
This capability is important because it helps organizations proactively defend against digital risks like phishing attacks, brand abuse, and counterfeiting. By identifying potential threats before they can be exploited, it strengthens an organization's overall security posture. ThreatNG's Domain Name Permutations capability provides a complete view of an organization's digital footprint and helps you respond swiftly to threats with actionable intelligence.
-
This capability is also known by terms like domain squatting detection, typosquatting analysis, or look-alike domain monitoring. Other approaches often involve manual searches or reactive monitoring, where threats are only identified after they have become active, requiring a more resource-intensive and often less effective response.
-
ThreatNG's Domain Name Permutations capability is different because it offers a customizable and comprehensive approach. It uses a packaged set of Top-Level Domains (TLDs) and Targeted Keywords, but also allows users to add their own to ensure the analysis is always relevant to their unique digital footprint and risk tolerance. This contrasts with solutions that may rely on static or limited lists. The platform's ability to provide IP addresses and mail records for taken domains also offers critical, actionable intelligence for immediate response.
-
Categorizing domain name permutations is critical because it helps you understand the specific methods attackers use to create fraudulent domains, allowing for more targeted and efficient threat detection and response. This prioritization is vital for allocating resources effectively and addressing the most critical risks first. A Homoglyph or Bitsquatting domain, for instance, may pose a higher risk due to its use in sophisticated phishing attacks, while a simple Dictionary Addition might be used for a fake support site. Categorization helps differentiate between these types of threats so you can respond accordingly.
-
The categorization of permutations is useful because it provides greater context and actionable intelligence. It allows a business to quickly differentiate a minor typo from a deliberate and malicious attempt at brand impersonation. This categorization provides a more proactive and nuanced approach to security. For example, a security team can use the categories to prioritize which threats to address first based on the known tactics of attackers. The classification of a fraudulent domain provides immediate insight into the potential purpose behind the manipulation, such as a Subdomain Impersonation used to mimic a legitimate service or a TLD-Swap for a fake login page.
-
An organization can use these categorizations to create automated workflows and targeted responses.
Brand Protection & Marketing: A brand protection team can use the Homoglyphs and TLD-Swaps categories to set up alerts for new domains that visually mimic their brand. When a new domain is flagged, the system can automatically send an alert to the legal team to begin a takedown process, protecting brand integrity and customer trust. Marketing can use the Available domains to register them proactively to prevent an attacker from using them in the future.
Security Operations (SecOps) & Incident Response: A SecOps team can prioritize new threats by the permutation category. A newly registered domain found in th Bitsquatting category might trigger an automated investigation via a SOAR platform, which would immediately check the IP address and mail record provided by ThreatNG to see if the domain is hosting a malicious site. If it is, the system could automatically push an alert to an incident response team, allowing for a swift and targeted defense before a phishing campaign is even launched.
Third-Party Risk Management: When vetting a new vendor, a due diligence team can use the domain permutation categorization to assess the third party’s digital footprint. By searching for permutations in categories like Subdomain Impersonation or Replacements related to the vendor's brand, the team can uncover hidden risks or past security incidents that the vendor might not have disclosed. This provides objective data to validate the third party's security claims and informs your decision on whether to partner with them.
-
This capability is crucial for a variety of roles within an organization. It's vital for External Attack Surface Management by helping to identify look-alike domains and potential threats before they become active attacks, which helps shrink the attack surface. For Digital Risk Protection and Brand Protection, it defends against brand impersonation and helps prevent phishing and counterfeiting. It's also important for Due Diligence and Third-Party Risk Management by helping you vet potential partners, assess their digital footprint, and monitor them for new threats.
-
The Domain Name Permutations capability is a critical part of the overall ThreatNG solution because it feeds into several key risk assessments and intelligence modules, enhancing the platform's ability to provide a comprehensive security posture evaluation. It's a core component of Domain Intelligence which in turn helps derive scores for BEC & Phishing Susceptibility, Brand Damage Susceptibility, and Data Leak Susceptibility. This capability also contributes to ThreatNG's overall mission of providing an all-in-one solution for external attack surface management, digital risk protection, and security ratings.
-
This capability complements other security solutions by providing proactive, external intelligence that helps identify threats before they are used in an attack. It can feed information to a SIEM or SOAR platform, allowing for automated investigation and response to a newly registered look-alike domain. For Incident Response teams, it provides actionable intelligence like IP addresses and mail records to accelerate their investigations. The solution also enhances Brand Protection services by identifying a broader range of complex domain manipulations, such as homoglyphs and bitsquatting, that may be missed by other tools. Additionally, it can benefit Vulnerability and Penetration Testing by identifying a client’s unknown or forgotten domains, expanding the scope of their work.