ThreatNG Two Way Tuesdays
Welcome to ThreatNG's new branded entertainment initiative, “Two-Way Tuesdays”, where we tell original narratives based on the lives of those in the Tech and Cybersecurity industries.
To bring these stories to life, we are asking our audience to provide personal profiles that will provide the insights that will fuel these narratives. To date, we have received many inputs. As you can imagine, we want dozens upon dozens more to help bring life to this new program.
Check out our profile participants below!

If you would like to be a part of future narratives, please answer the questions in the form provided below. THANK YOU!
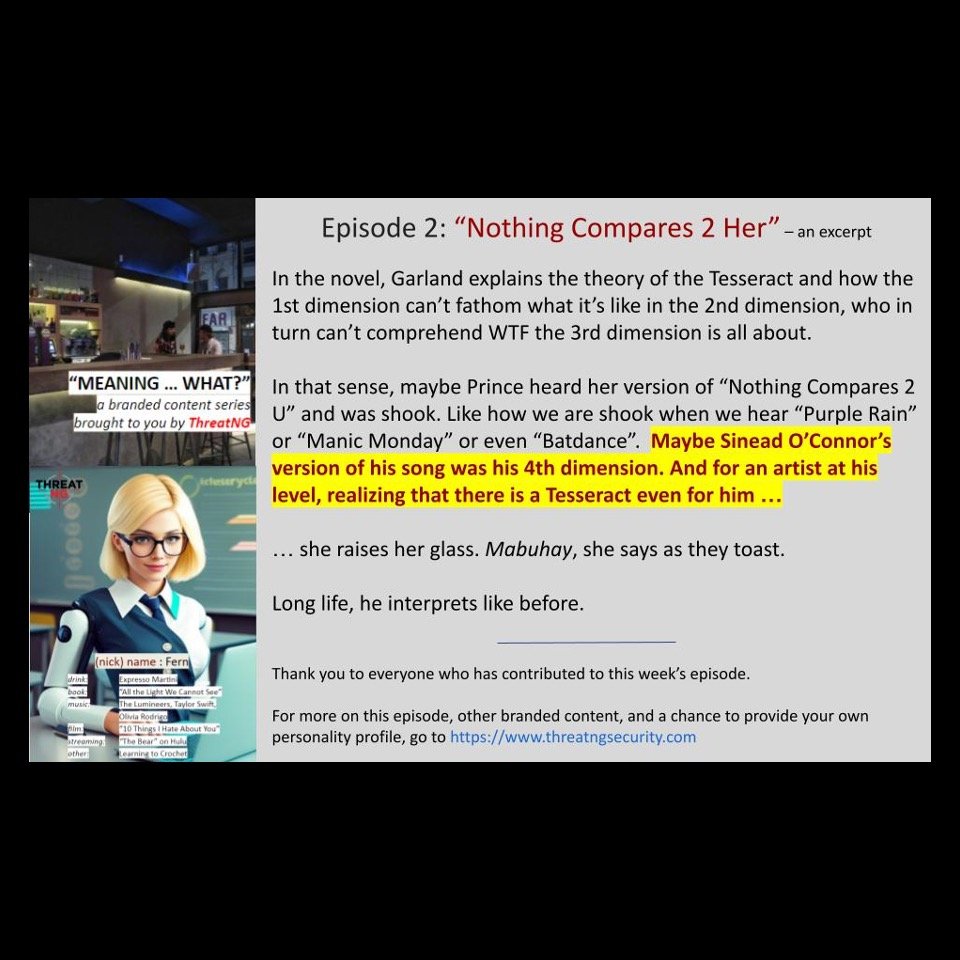
I AM NOT A BOT: Episode 1 “fr”
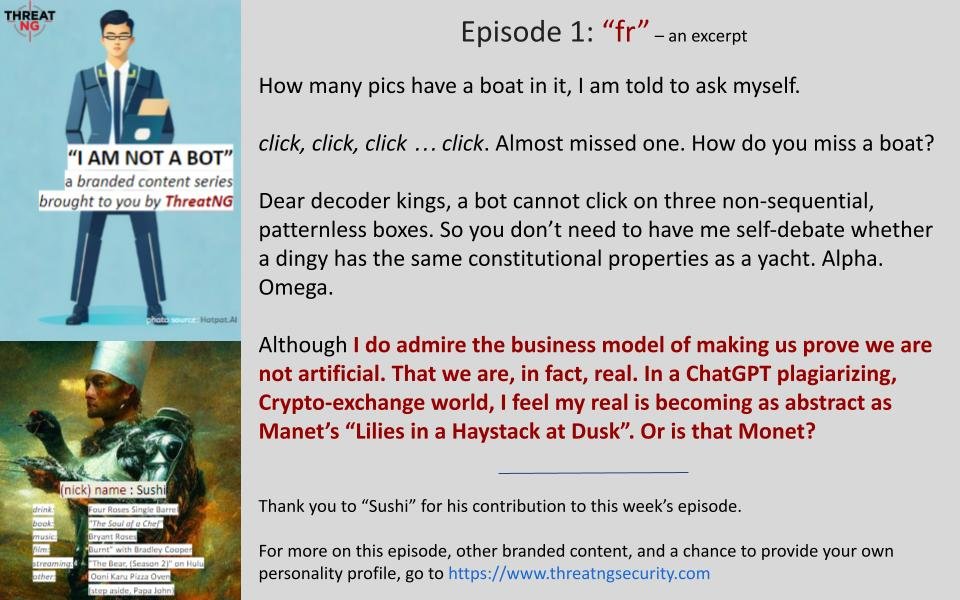
How many pics have a boat in it, I am told to ask myself.
click
click
click
…
click
Almost missed one. How do you almost miss a boat?
Dear decoder kings, a bot cannot click on three non-sequential, patternless boxes. So you don’t need to have me self-debate whether a dingy has the same constitutional properties as a yacht. Alpha. Omega.
Although I do admire the business model of making us prove we are not artificial. That we are, in fact, real. In a ChatGPT plagiarizing, Crypto-exchange world, I feel my real is becoming as abstract as Manet’s “Lilies in a Haystack at Dusk”. Or is that Monet?
I finally Zoom into my Cybersecurity class, already in progress. I hear the teacher ask the cohort,
“A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during an incident response. Which of the following procedures is the NEXT step for further investigation?
A. Data Carving
B. Timeline Construction
C. File Cloning
D. Reverse Engineering”
JZ99 jumps into the Zoom chat and types, "A. Carving = Memory.”
Unbeknownst to our teacher, a few of us have a concurrent Discord chat that trolls our class’s progress, or lack thereof in this case.
Various “X”’s, buzzer sounds, and frowny faces emote that we disagree with JZ99.
Our gal from Nepal quick clicks into the Zoom chat, “Data Carving is what you do to get the evidence. Reverse Engineering is what you do NEXT with this evidence.”
"CompTIA out to obfuscate again,” Edamame Discords.
NotSoShi adds, “Can’t you just ask us if we know what Data Carving is?”
ZaeZae subtracts, "CompTIA sucks.”
This last response gets a series of supportive finger points and “fr” responses. I’m one of the pointers, even though I feel myself drifting away from this online conversation.
The class continues. My self-diagnosed ADHD, on the other hand, carries me to my origin story.
I didn’t have a big a-ha moment when I decided to take this path less traveled that is Cybersecurity training. Somewhere between the pouring of the ½ oz of maple syrup and the mint leaf garnering on my umpteenth, ticketed Mojito, I simply decided that this was no longer the way.
I admit I do miss toasting the newlywed couple and their wedding party with a line of Love Bites. And, yes, few things in life are more intoxicating than pouring a party of 21’s their first Bikini Martinis. I also wish I could cocktail an Old Fashioned for my father again, but as he would say, “Your body knows when it’s time to go before any clock could tell you.”
This is why I have about two dozen tabs open on my screen today. Everything from the “Advent of Cyber” with TryHackMe to “Certified Breakfast” with Andrei Ciorba to Hacksplaining.com at the ready for translation purposes. All with Tash Sultana’s Tiny Desk performance on Youtube serenading this session, which somehow helps me stay attached to this new task and purpose.
I smile as I see that ZaeZae has once again incited our Discord crew. And once more, he garners finger point after finger point of support.
I smile wider, knowing that I made the right move.
Despite not really knowing what ZaeZae is talking about, I top off this conversation with my own ...
fr
fr
fr