ThreatNG Two Way Tuesdays
Welcome to ThreatNG's new branded entertainment initiative, “Two-Way Tuesdays”, where we tell original narratives based on the lives of those in the Tech and Cybersecurity industries.
To bring these stories to life, we are asking our audience to provide personal profiles that will provide the insights that will fuel these narratives. To date, we have received many inputs. As you can imagine, we want dozens upon dozens more to help bring life to this new program.
Check out our profile participants below!

If you would like to be a part of future narratives, please answer the questions in the form provided below. THANK YOU!
I AM NOT A BOT Episode. 3: “The Birthday Paradox”



I smirk at the Brute Farce Attack online headline while waiting for my teacher to let me into today’s Zoom class,
DIVERSE CYBERSECURITY PANEL HOSTS FIVE DIFFERENT KINDS OF WHITE MEN, AND ONE PAIR OF RAINBOW SOCKS.
Seconds later, popups of true diversity appear on my screen, including various shades of African, Asian, and Latin American.
This Cybersecurity program I’m in is designed to give minorities access to advanced tech training – education being the ultimate hack into the good ol’ boy network.
The face of my father pops up in the Zoom box of my mind. Today’s version is a lot younger than usual.
When he came to America in the late 1960s, my father struggled as a medical resident, mainly because he was earning just $150 a month. To support my mom and my older sister and my older brother, he had to take a second job.
His American counterparts, on the other hand, made $1500 a month. No second jobs needed. Probably got their rainbow socks for free.
“The Birthday Paradox,” my teacher opens with, “is a study of probabilities. Sometimes an event is more likely to occur than we believe it to be.”
Our cohort started with 22 students. Four abandoned ship after the first two weeks. What is the occurrence probability of such a drop off? High, I think to myself.
“In this case, if you survey a random group of just 23 people, there is a 50–50 chance that two of them will have the same birthday.”
We try it. No luck. None of our birthdays match. Maybe because we are down to 19 Zoom boxes.
“Ok. Now everyone think of a family member. A brother. A sister. One of your parents. One of their birthdays will likely match one from --”
-- Edamame chimes in. ZaeZae’s birthday matches his wife’s.
I type into the Zoom chat that NotSoShi’s birthday is July 1st. My father’s birthday.
“The occurrence probability of a birthday match moves close to 100% if you expand the room to 100 people,” my teacher says. “From 50/50 to almost 100 with a simple expansion.”
Various heads nod in their Zoom boxes.
“There is a high probability of a match because there are a finite number of options. There are only 366 possible birthday dates, which makes it easier to find someone just like you.”
“There is no one in the world like me,” ZaeZae touts on Discord.
“And this all relates to Password Cracking how?” my teacher asks.
An awkward silence follows.
“Think of what we learned yesterday about hashing. Remember why we hash, the importance of encryption.”
Try as I might, I can’t help but mentally detach from class, as I tend to do.
I do hear something about hashing algorithms.
I do hear something about taking an input of any length and producing an output of a fixed length.
I do hear something about the birthday attack and the creation of hash collisions.
I do smile as I see that ZaeZae has typed, “Uh … huh?” into the Zoom chat.
I focus on the “huh?”, which transports me to my parents and their “huh?”
I am transported back to me. Baby me that is, wrapped in swaddling clothes. That's because I was a “huh?” A mistake. An oops. My sister is 12 years older than me. My brother 10.
I look at a baby me and cry to myself, I been done trying to find that someone in the world like me.
I smile again when I look at my head. I smile at the fact that all babies are given the same rainbow colored beenie to warm their heads at birth. A lazy attempt to connect us all.
My mind’s eye clicks on to the rainbow socks crew from this morning’s Brute Farce Attack meme. I start to think that the biggest problem in the Cybersecurity industry is related to the Birthday Paradox we are studying. The biggest problem is that you have the same finite set of good ol’ boys’ minds trying to solve an infinite number of problems in the Infosec universe. And to no one’s surprise, these limited minds are failing.
Alpha. Omega.
Cybersecurity breaches have cost American companies billions of dollars over the last few years. According to the U.S. Treasury’s Financial Crimes Enforcement Network (FinCEN), nearly $600 million was paid out by US victims of Ransomware in the first half of 2021 alone.
Black Hats, as of course they are labeled, have tapped into Uber databases and have snuck into Los Angeles’s public school district. Just the other day, there was the Southwest holiday travel debacle caused by malware. Today, that was elevated into a nation-wide shutdown of air traffic control across all airlines.
A new McKinsey research study alarms that Cyberattacks have caused $2 trillion dollars of damage in 2022.
The same finite, exclusive set of “white hats” are losing to a rainbow of adversaries who are constantly trying to think up new ways to digitally attack us with each sun is shining and each birds are chirping.
Or … are these white hats covertly trying to cash in on the $2 trillion market opportunity that is cybersecurity technology and cybersecurity service?
“I don’t know, “ ZaeZae answers out loud to another of our teacher’s questions.
There are an infinite number of questions in this ever morphing industry. The good news, however, is that there really is just one answer to them all. One solution. One way to combat all the hacks and all the bad actors we have discussed over the past few weeks.
And if you think about it, there is just one way to address all of the ‘huhs?” and all the accidental collisions and all of the purposeful paradoxes this country has hashed out on the regular.
One answer. One understanding. And that answer, that understanding is that DIVERSITY MATTERS.
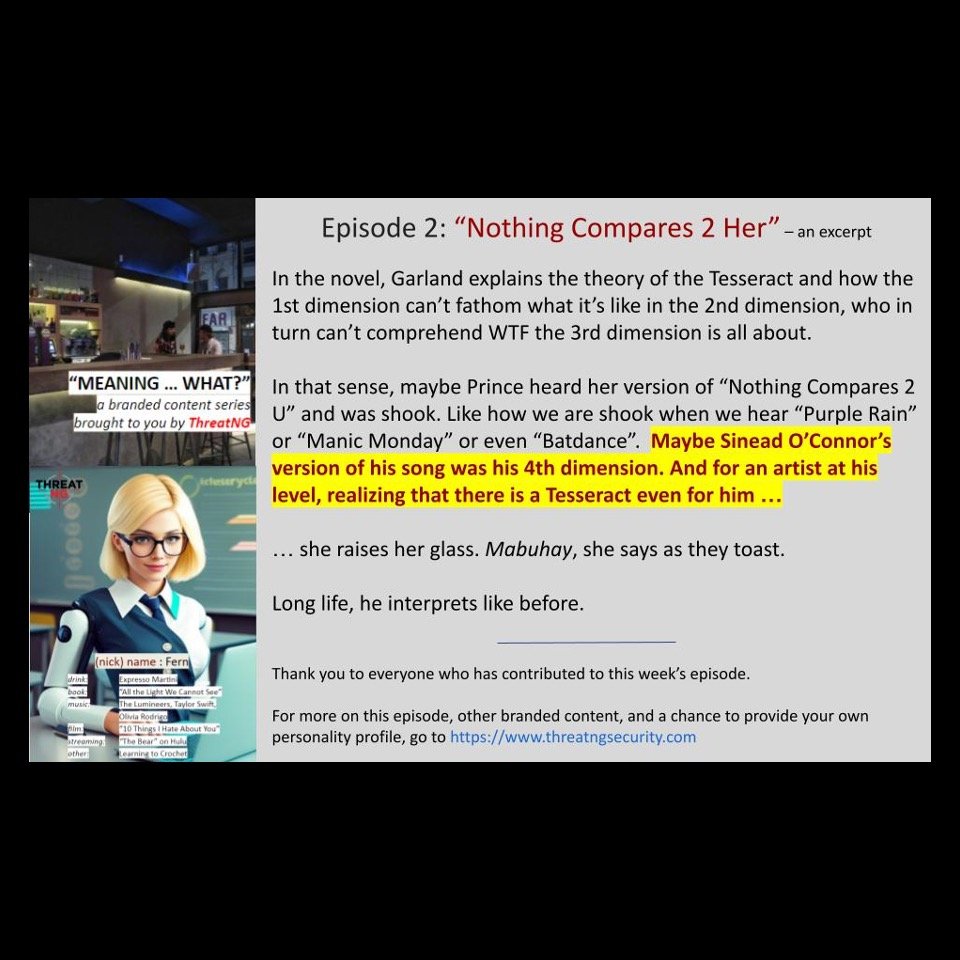
I AM NOT A BOT: Episode 1 “fr”
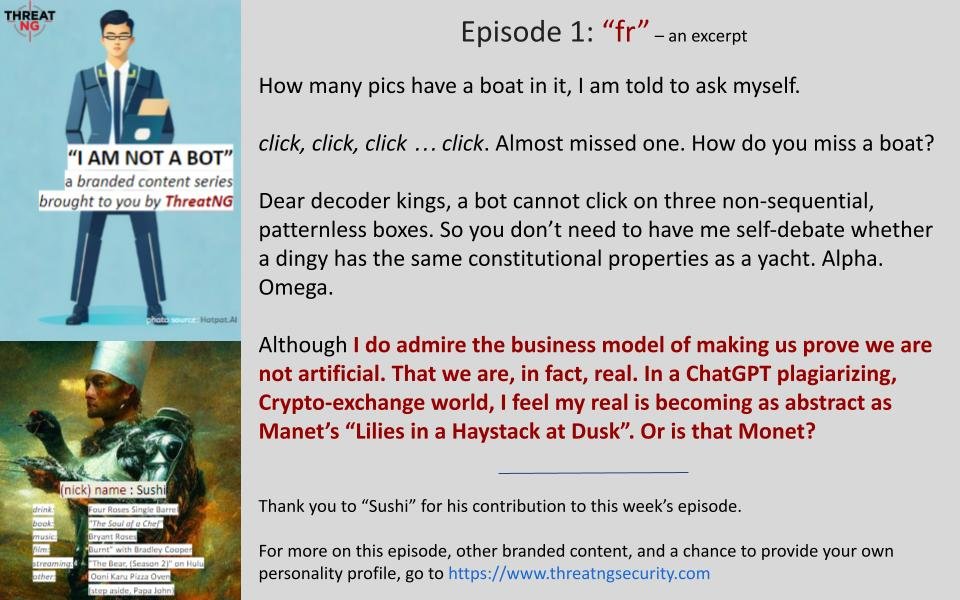
How many pics have a boat in it, I am told to ask myself.
click
click
click
…
click
Almost missed one. How do you almost miss a boat?
Dear decoder kings, a bot cannot click on three non-sequential, patternless boxes. So you don’t need to have me self-debate whether a dingy has the same constitutional properties as a yacht. Alpha. Omega.
Although I do admire the business model of making us prove we are not artificial. That we are, in fact, real. In a ChatGPT plagiarizing, Crypto-exchange world, I feel my real is becoming as abstract as Manet’s “Lilies in a Haystack at Dusk”. Or is that Monet?
I finally Zoom into my Cybersecurity class, already in progress. I hear the teacher ask the cohort,
“A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during an incident response. Which of the following procedures is the NEXT step for further investigation?
A. Data Carving
B. Timeline Construction
C. File Cloning
D. Reverse Engineering”
JZ99 jumps into the Zoom chat and types, "A. Carving = Memory.”
Unbeknownst to our teacher, a few of us have a concurrent Discord chat that trolls our class’s progress, or lack thereof in this case.
Various “X”’s, buzzer sounds, and frowny faces emote that we disagree with JZ99.
Our gal from Nepal quick clicks into the Zoom chat, “Data Carving is what you do to get the evidence. Reverse Engineering is what you do NEXT with this evidence.”
"CompTIA out to obfuscate again,” Edamame Discords.
NotSoShi adds, “Can’t you just ask us if we know what Data Carving is?”
ZaeZae subtracts, "CompTIA sucks.”
This last response gets a series of supportive finger points and “fr” responses. I’m one of the pointers, even though I feel myself drifting away from this online conversation.
The class continues. My self-diagnosed ADHD, on the other hand, carries me to my origin story.
I didn’t have a big a-ha moment when I decided to take this path less traveled that is Cybersecurity training. Somewhere between the pouring of the ½ oz of maple syrup and the mint leaf garnering on my umpteenth, ticketed Mojito, I simply decided that this was no longer the way.
I admit I do miss toasting the newlywed couple and their wedding party with a line of Love Bites. And, yes, few things in life are more intoxicating than pouring a party of 21’s their first Bikini Martinis. I also wish I could cocktail an Old Fashioned for my father again, but as he would say, “Your body knows when it’s time to go before any clock could tell you.”
This is why I have about two dozen tabs open on my screen today. Everything from the “Advent of Cyber” with TryHackMe to “Certified Breakfast” with Andrei Ciorba to Hacksplaining.com at the ready for translation purposes. All with Tash Sultana’s Tiny Desk performance on Youtube serenading this session, which somehow helps me stay attached to this new task and purpose.
I smile as I see that ZaeZae has once again incited our Discord crew. And once more, he garners finger point after finger point of support.
I smile wider, knowing that I made the right move.
Despite not really knowing what ZaeZae is talking about, I top off this conversation with my own ...
fr
fr
fr